SSH is a wonderful tool. It allows you to run commands on a remote host, either manually, or from scripts. Obviously, since it’s a remote connection, you must authenticate yourself to the remote host. There are several ways of doing this.
When using SSH in a script, most pages tell you to use public keys. While this is an excellent idea, it’s sometimes just not possible due to policy. This Expect script fakes a regular username-password login
#!/usr/bin/expect -f
set target [lindex $argv 0]
set password [lindex $argv 1]
set command [lindex $argv 2]
spawn ssh $target $command
match_max 100000
# Look for passwod prompt
expect “*?assword:*”
# Send password aka $password
send — “$password\r”
# send blank line (\r) to make sure we get back to gui
send — “\r”
expect eof
This script can be run like this:
./ssh-passwd.ex root@192.0.2.1 password “ls /root”
Posted by Niobos on 2010-02-16 at 15:46 under Networking & Security.
Tags: script, SSH
No comments.
I just read this message by Mark Andrews on the BIND mailing list. It explains the possible issues with DNSSEC and over-protective firewalls, giving test-commands to verify your setup. This post is also interesting for regular DNS traffic, since a firewall doesn’t know the difference.
Continue reading ‘DNS(SEC) – Firewall issues’ »
Posted by Niobos on 2010-02-10 at 19:03 under Networking & Security.
Tags: DNS, dnssec, firewall, links, NAT
No comments.
DNSSEC, short for DNS security, provides a security extension to the all important DNS system. A nice intro can be found on wikipedia. This is a part of a series on DNSSEC:
- The RRSIG record
- The NSEC and NSEC3 record
- The DNSKEY and DS record
- Implementation
Time to put things together and setup a simple DNSSEC secured zone using BIND. Instead of providing a walkthrough, I’m just going to refer to the DNSSEC HOWTO (local mirror of the PDF version) of NLnetLabs. It provides a very thorough explanation of the whole DNSSEC concept, including copy-paste examples to try out. Also, it goes more into practical details such as key rollover, the benefits of using two keys (a Zone Signing Key, or ZSK, and a Key Signing Key, KSK).
Continue reading ‘DNSSEC – Implementation’ »
Posted by Niobos on 2010-01-24 at 14:13 under Networking & Security.
Tags: DNS, dnssec
No comments.
DNSSEC, short for DNS security, provides a security extension to the all important DNS system. A nice intro can be found on wikipedia. This is a part of a series on DNSSEC:
- The RRSIG record
- The NSEC and NSEC3 record
- The DNSKEY and DS record
- Implementation
To verify the digital signatures inside the RRSIG records, the client needs to have access to the corresponding public key. What better mechanism than DNS itself could be used to convey this information to the clients? Public keys are stored in DNSKEY records inside the zone. To facilitate key rollovers, new keys are added ahead of time, while old keys remain in the zone until all entries have expired in the caches. Continue reading ‘DNSSEC – The DNSKEY and DS record’ »
Posted by Niobos on 2010-01-22 at 17:13 under Networking & Security.
Tags: DNS, dnssec
No comments.
DNSSEC, short for DNS security, provides a security extension to the all important DNS system. A nice intro can be found on wikipedia. This is a part of a series on DNSSEC:
- The RRSIG record
- The NSEC and NSEC3 record
- The DNSKEY and DS record
- Implementation
While the RRSIG record allows you to verify the authenticity of returned records, there is still a gap remaining. What if the requested name does not exist? Since the DNS server replies with an empty answer section, there is nothing to sign. That’s where NSEC (or its brother NSEC3) comes into play. An NSEC record (Next SECure) states the range of names that do not exist. By signing this NSEC record by a corresponding RRSIG record, one can prove that a domainname does in fact not exist.
Posted by Niobos on 2010-01-20 at 17:11 under Networking & Security.
Tags: DNS, dnssec
No comments.
DNSSEC, short for DNS security, provides a security extension to the all important DNS system. A nice intro can be found on wikipedia. This is a part of a series on DNSSEC:
- The RRSIG record
- The NSEC and NSEC3 record
- The DNSKEY and DS record
- Implementation
The RRSIG record is the basic building block of DNSSEC. It accompanies every Resource Record Set (RRset) and provides a digital signature over the provided data. This record is only supplied if the client indicates that it understands DNSSEC. A client does so by setting the DO (DNSSEC OK) flag (part of EDNS). If the server adds this record, it can be used to prove that the received data is authentic and hasn’t been tampered with (or prove the opposite). If, on the other hand, the response doesn’t contain RRSIG records, there are two possibilities. Probably the zone just doesn’t use DNSSEC, but it’s also possible that the response has been tampered with and had its RRSIG removed. Unless you have some prior knowledge, it’s impossible to know which case you’re in. This should be solved once the root-zone becomes signed in July 2010.
Continue reading ‘DNSSEC – The RRSIG record’ »
Posted by Niobos on 2010-01-17 at 11:34 under Networking & Security.
Tags: DNS, dnssec
No comments.
I still have a perfectly working Windows Mobile PDA-phone. I use a program called PIM Backup to make backups of the databases such as calls, SMSes (text messages), contacts, calendar, …. The program can generate either a binary backup, or a more readable backup. I use the latter one, so I could unpack the backup on my desktop computer and use it as an archive. The generated backup files have a .pib extension. The file itself is a ZIP-file containing the different parts of the backup (calls, contacts, …) as separate files.
Posted by Niobos on 2010-01-03 at 19:41 under Uncategorized.
Tags: PDA, WindowsMobile
No comments.
WordPress seems to have its security a bit too tight to let me do my job: I wanted to upload a Perl-script, but instead I got
File type does not meet security guidelines.
A bit of googling got me to Kristof Coomans’ blogpost which pointed me to the PJW Mime Config plugin. This plugin allows you to add custom file extensions and their corresponding MIME-types to be accepted as uploads.
Posted by Niobos on 2010-01-03 at 19:26 under Networking & Security.
Tags: mime, WordPress
No comments.
Just before the holidays, we got ourselves a Dreambox DM8000, an HD-capable set-top box and personal video recorder. The hardware features look good: twin DVB-S2 tuner build in, 2 free slots for additional tuners, e.g. for DVB-T or -C reception. It has 4 CI (Common Interface) slots for Conditional Access Modules (CAM’s), and 2 smartcard readers. Under the hood is a 400MHz MIPS processor, running a special linux, named “Enigma2” from a flash-chip. An optional harddisk and (slimline) DVD-reader are also available, but you have to build them in yourself. Doing so was really easy, as all screws and connectors are provided.




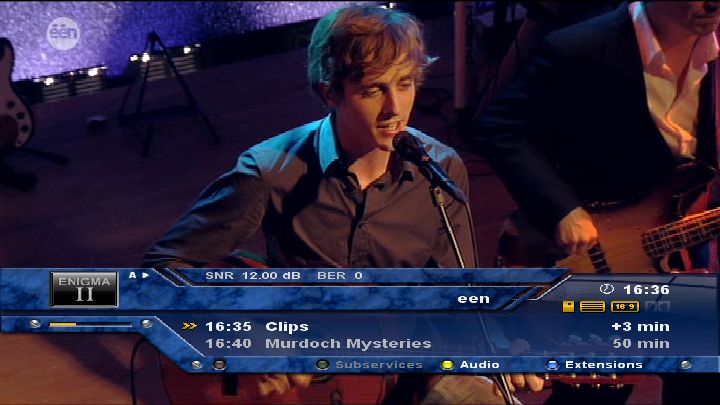
The installed software is descent, tunes fast and didn’t crash (yet). It supports decoding multiple channels from a single multiplex (known as multirec in the MythTV-world). The manual (local copy) could be more thorough, though. The recording-scheduling simply sucks, especially if you’re used to MythTV’s scheduling.
Continue reading ‘Dreambox DM8000’ »
Posted by Niobos on 2010-01-02 at 17:48 under Multimedia.
Tags: dreambox, DVB-S, DVB-T, MythTV
3 Comments.
A half year ago, I blogged about a web-based RSS-reader. Recently I found an alternative product, tt-rss. It has an AJAX-based user interface which is of course much slicker, but it also gives more features, such as:
- Categories
- Scoring: use regular expressions to hide/highlight certain posts
Posted by Niobos on 2009-12-29 at 21:32 under Networking & Security.
Tags: links, rss
No comments.





